What motivates cybercriminals to target and attack corporations and government entities? The obvious answer is money. However, is there more to it than that? As a cybersecurity company, we wanted to know, and we took a unique, straightforward approach to getting this answer: we asked the cybercriminals themselves!

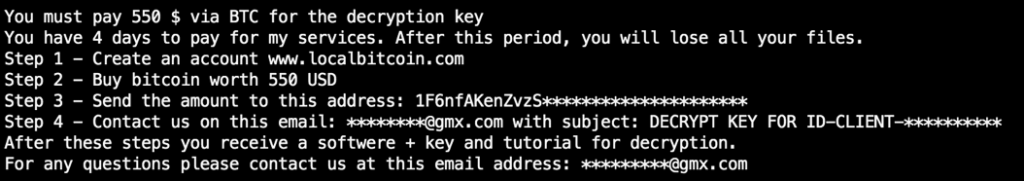
But first, how to find them? We could go into forums and look for these individuals, but this would be time-consuming and odds were slim that we would find the right person. So, we took samples of recent ransomware and examined the ransom note, which like most notes contained an email address where to send your payment and even a help desk type of email address for questions.
We looked at months of unique ransomware samples and extracted either the images or the notes that contained the contact addresses. As new ransomware families popped up in our tracker, we verified them and added the addresses — because fresh attacks made it likely the authors would interact with us.
After accumulating these addresses, we sent emails asking if they would answer a few questions. Interestingly enough, when we sent these emails, we found that 30 percent of the addresses were either fake or nonexistent. So, in these cases when files were encrypted and the victim decided to pay, using email to send evidence of payment was useless. The money was gone (as well as the files).
During the first week of research, we received answers from some of the actors, but most were not willing to cooperate. That’s no surprise: They were cautious about revealing their identity.
During the second week, we had better luck and started to chat with a few. That number grew, and after a few weeks we had a great collection of conversations going.
“Fast, easy and safe”
When we asked why they started a career in ransomware, most answered with variations of “enough money” and “fast, easy and safe,” especially when using anonymous email services and cryptocurrency for payments.
Never pay the ransom
To reduce your risk of picking up ransomware: Keep your OS, security and application software up to date; regularly back up data stored on your computer; exercise a healthy dose of skepticism even when you see messages that appear to come from legitimate sources; and do not click on links or open files from unknown names or organizations.
>> If you do get infected, don’t pay the ransom <<
As we saw with our research, it most likely will not get you your files back. Plus, your payment will help fund the cybercriminals’ next attack.
Report the infection to the authorities and visit NoMoreRansom.org to see if a decryption tool is available.
Homemade vs. off the shelf
Most of the actors we spoke with wrote their own ransomware. They had looked at published source code, but were clever enough to come up with their own variants that contained new techniques or different approaches to keep detections low. The longer they stayed out of sight of endpoint security solutions, the longer their opportunity to make money.
Spending their ill-gotten gains
We found that they spent the revenue gained from their campaigns in various manners: travel, cars. One responder had many affiliates working for him and was planning to buy a house. One of the most surprising answers was to “pay off debts.”
Willing to negotiate
Although they often have the image of being ruthless, almost all of them claimed a willingness to negotiate the ransom price if the victim could not afford to pay the demanded amount.
Tracking the authors
One of the actors told us he not only sends ransomware, but also sells botnets and other fraud-related services. He was open to sharing more information, so we kept the conversation going. We learned he was not a very experienced actor since he gave clues to his whereabouts. In one of the conversations, he shared some examples, but the data was not scrubbed. By correlating the data he provided with other information, such as email time zones and mistakes in his English, we traced him to Dakar, the capital of Senegal, in West Africa.
An eye-opening experience
One of the interesting findings was that cybercriminals have a sense of absolute safety when conducting criminal operations. Cybercrime is a crime like no other, perceived as low-risk with high returns, which contributes to its rapid growth. However, this is misguided thinking. Law enforcement agencies around the world are teaming up with academic institutions and cybersecurity companies, including McAfee, to take down these individuals.
In 2016, a massive spam campaign struck the Netherlands. Files were encrypted and ransom notes appeared. The Dutch High Tech Crime Unit began an investigation and requested the help of McAfee’s Advanced Threat Research team to assist in identifying samples and answering questions.
We were able to determine that the criminals behind the Netherlands campaign were also responsible for spreading ransomware throughout Europe and the U.S. Most importantly, we were able to determine these actors were operating in Romania.
Learn more about cybersecurity
Insights on Data Protection on Xerox.com.
More articles about security on this blog.
Read Securing Tomorrow, a blog from McAfee.
The arrests
In mid-December 2017, Romanian authorities stormed into the houses the suspects were working in and arrested three individuals for allegedly spreading CTB Locker ransomware. During this law enforcement operation called “Bakovia,” six houses were searched, whereby the investigators seized a significant amount of hard drives, laptops, external storage, cryptocurrency mining rigs and hundreds of SIM cards. In a parallel ransomware investigation, two other suspects from the same criminal group were arrested at the airport in. Bucharest
This law enforcement action emphasizes the value of public-private partnerships, and underscores the determination behind the McAfee mantra, “Together is power.”
CTB locker
CTB Locker, also known as Critroni, is known as one of the largest ransomware families — helping to drive a new ransomware surge of 165 percent in 2015, and earning a spot as No.1 just a year later. Operation Tovar, in which law enforcement agencies took down the infrastructure responsible for spreading CryptoLocker, created a need for more malware — CTB Locker and CryptoWall malware families helped to fill the gap.
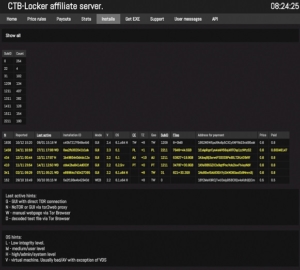
In June 2014, the CTB Locker authors began to advertise the malware family on the underground scene at a cost of $3,000 USD, where people could buy the first versions for $1,500 USD. The authors also offered an affiliate program, which made CTB Locker infamous. By sharing a percentage of the received ransoms, the affiliates ran the greater risk — because they had to spread the ransomware — but they also enjoyed the higher profits. By using exploit kits and spam campaigns, the malware was distributed all over the world, mostly targeting “Tier 1” countries, (those in which the victims could afford to pay and most likely would pay the ransom). Midway through 2015, we gained unique information from an affiliate server that helped us tremendously in the subsequent investigations.
From the editor: This article includes excerpts from “McAfee Labs Advanced Threat Research Aids Arrest of Suspected Cybercrime Gang Linked to Top Malware CTB Locker,” which was published in Securing Tomorrow, a McAfee blog, on December 20, 2017.



